RYAN G. COX
> Building secure systems and innovative solutions at the intersection of technology and entrepreneurship. Focused on creating meaningful impact through technical excellence and strategic vision.
[ABOUT_ME.SYS]

[PORTRAIT_LOADED]
> I am a cybersecurity professional with over 5 years of experience building and securing enterprise systems across multiple industries.
> My expertise spans threat detection, incident response, and security architecture, with a particular focus on developing innovative solutions that balance security with usability.
> As an entrepreneur, I have founded the first Security Incident Response platform to combine Inicdent Management and Post-Mortem Frameworks into a single platform, enabling security teams to take control of their Incident Response function with performance data to maximize efficiency and ensure continuous improvement..
> I feed my passion for mentoring the next generation of cybersecurity professionals and sharing knowledge through my weekly newsletter, the Cybersec Cafe, which covers various topics in the cybersecurity space.
> When not defending digital infrastructure, I enjoy exploring new technologies, contributing to the security community, and building tools that make security more accessible.
[ENTREPRENEURIAL_ENDEAVORS.SYS]
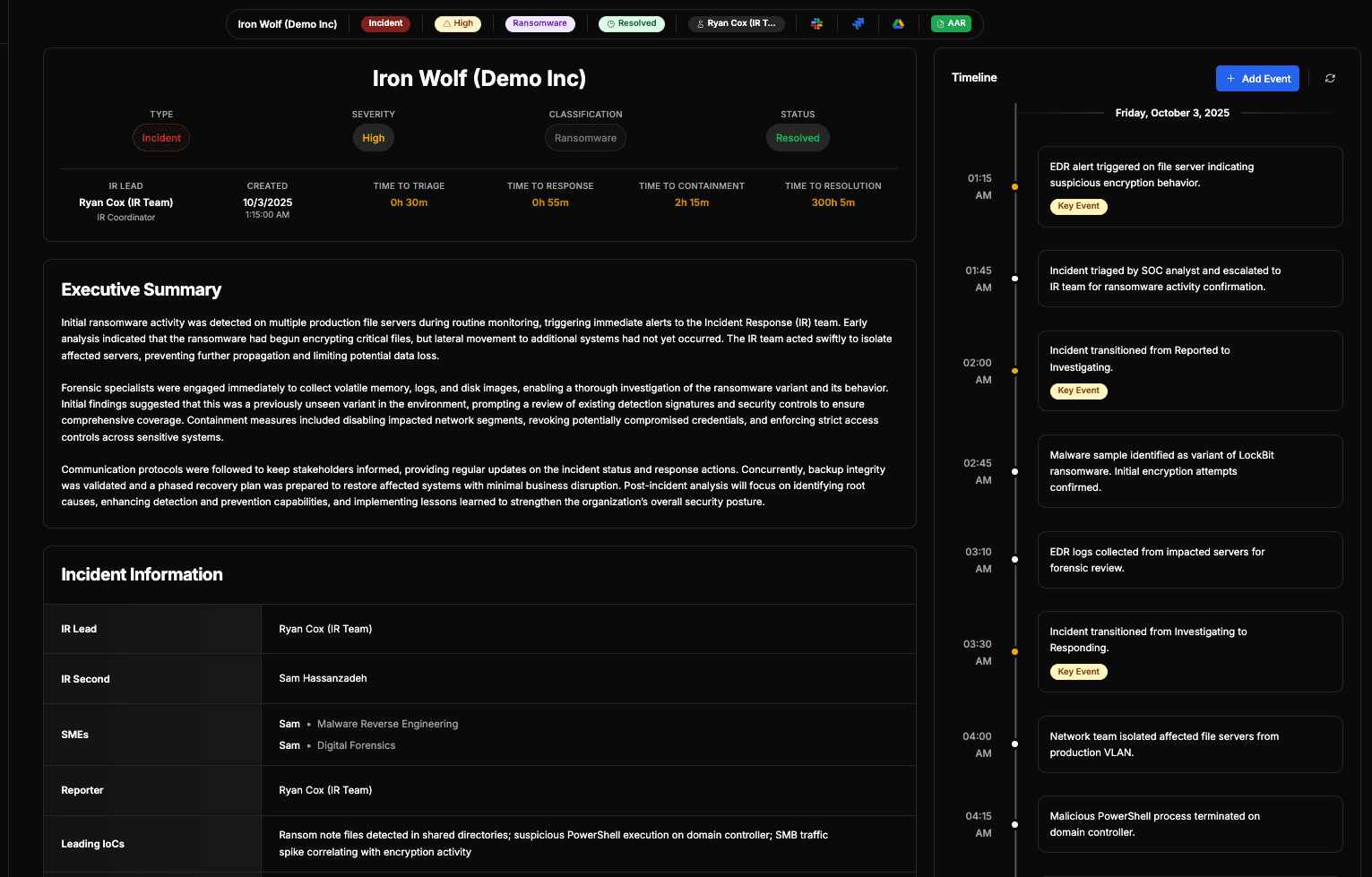
[IRHQ.SYS]

> The first Security Incident Response platform to combine Incident Management and Post-Mortem Frameworks into a single platform.
> Streamlines incident management workflows, automates response procedures, and provides real-time collaboration tools for security teams.
> Track incident trends, map to MITRE ATT&CK, and monitor root cause analysis to prevent future incidents and burnout.
[EDUCATION.SYS]
Bachelor of Science, Computer Science, Informatics
[PROFESSIONAL_EXPERIENCE.SYS]
Deteection and Response Security Engineer
> Act as a Security Engineer for the Detection and Response team, responsible for the detection and response of security incidents.
Senior Security Operations Engineer
> Assumed full ownership of Security Operations function, driving strategic direction and team management (4 reports) during an ongoing leadership gap.
Security Engineer
> Detection Engineering, SOAR & Automation, Incident Response, Threat Hunting & Security Testing, Leadership & Strategic Initiatives
Security Engineer
> Developed custom, automated solutions for network visibility and SOC operations.
Software Engineering Intern
> Developed mobile iOS applications and maintained legacy systems.
[SIDE_PROJECTS.SYS]
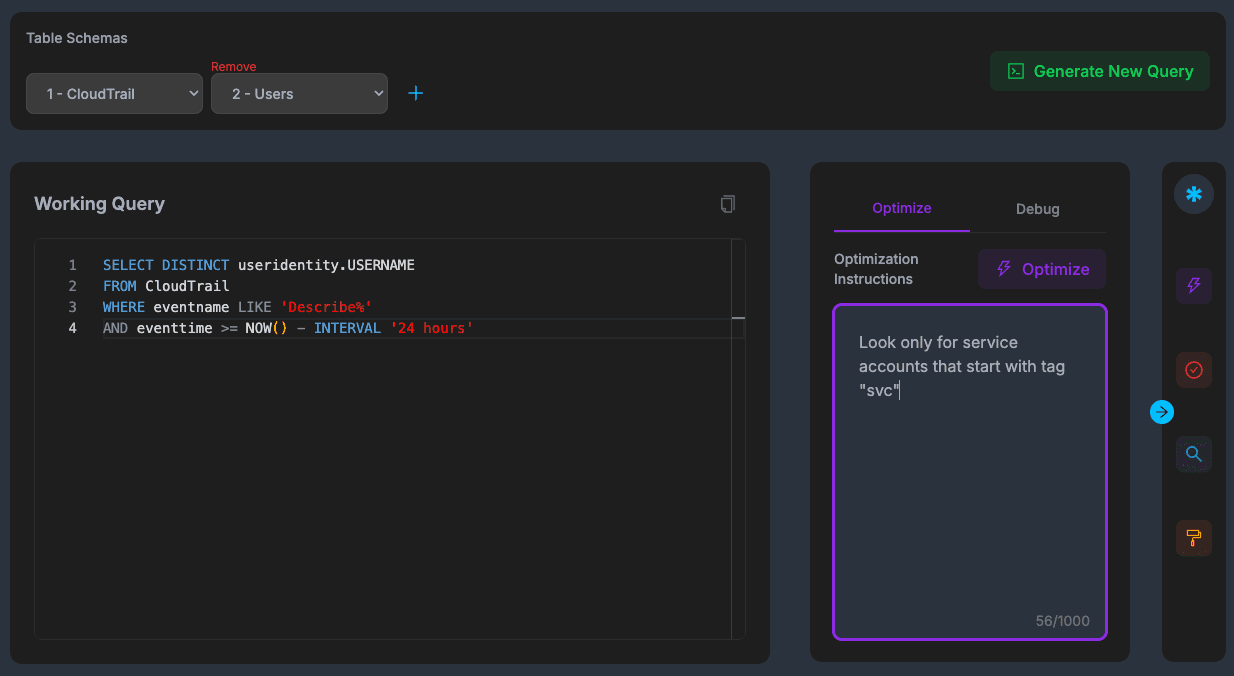
> A unified environment where all your query tools live together in one sleek interface. Write, optimize, and validate your queries with AI-powered features at every step.

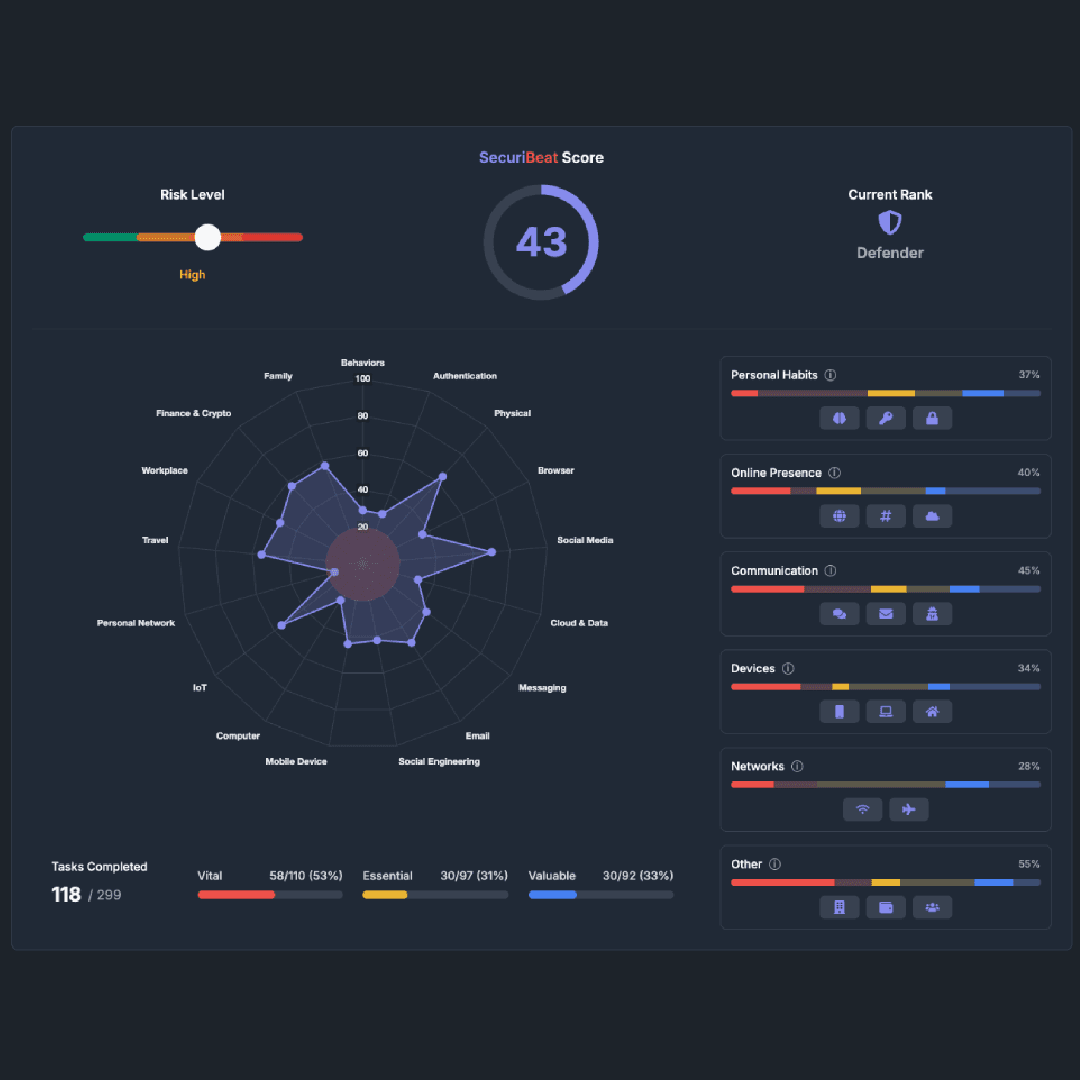
> Overwhelmed by digital security? Break down complex security practices into simple, actionable steps so you can build confidence in your personal cybersecurity decisions.